Permissions
enTermX privilege is an entity to describe fine-grained access to the resource or group of resources. Attribute-based access control (ABAC) is used to access granting.
The privilege description includes the following attributes:
Categorywith values “CodeSystem”, “ValueSet”, “ConceptMap”, any of CodeSystem or ValueSet or ConceptMap, and “admin”.Actionwith values “view”, “edit”, “publish”Resourcesany resource from the list of code systems, value sets, and concept maps.
Example of privilege configuration
| Decsription | Access configuration |
|---|---|
| The viewer of any resource | Category=any, Action=view |
| Editor of any CodeSystem | Category=CodeSystem, Action=edit |
| Publisher of the 2 exact value sets | Category=ValueSet, Action=publish, Resources=[languages,publication-status] |
| Superuser access | Category=admin |
Every user may have one or many privileges.
Information about user privileges comes through federated services proxy, where federated services proxy is OpenId Connect compatible SSO server (for example Keycloack) connected to LDAP or Active Directory.
After login application maps user groups to KTS privileges and uses this information during the user session.
Diagramm below explains how privileges work.
Default configuration
We provide default configuration suitable in the environment with a limited number of terminology editors.
Default installation contains 4 privileges:
kts-viewerProvides read access to all resources in the terminology server.kts-editorGives the permission to view, create and modify all resources, incl import ability.kts-publisherSame as editor with permission to publish resources.kts-adminThe user can perform all actions in the application.
Setup for your federated services
It includes 3 steps:
- Create user groups in your LDAP or Active directories with the same names of the privileges
- For example in the default configuration.
- The simplest setup may include only
kts-admingroup. - In the case of your specific policies, you can rename default privileges.
- Assign users to the created groups.
- Configure OpenId Connect compatible SSO (for example Keycloak) to use your federated setup.
Privilege management
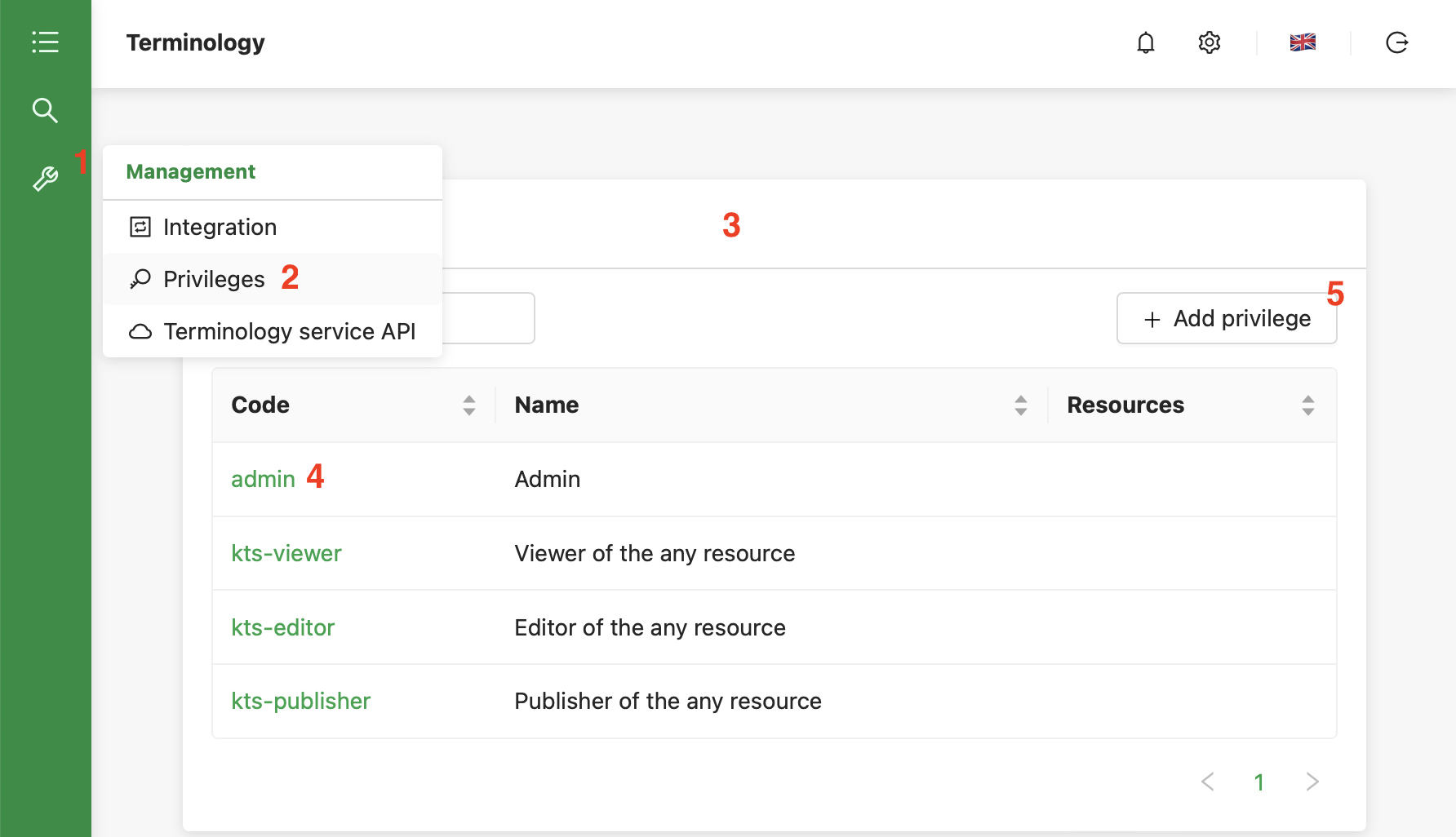
Select Menu -> Tools (1) -> Privileges (2). The list of privileges will be shown (3).
Click on the privileges code (4) to redirect to the detailed privilege view.
Button “Add privilege” (5) redirects to adding the new privilege.